Report
On the Ascent
via the central rib of the northern wall of the eastern spur of Mt. Aikuayvenchorr (Eastern) (858 m), "Lis" route, category 2B, Aikuayvenchorr ridge, Khibiny Mountains
March 25, 2017 (first ascent)
Leader: Orlov V.S. Coach: Proklov V.G.
Arkhangelsk, 2017
Ascent Passport
- Kola Peninsula, Khibiny mountain range. Classification table section number: # 8.6.2.
- Route name — "Lis", Aikuayvenchorr Eastern, 858 m, via the central rib of the northern wall of the eastern spur.
- Proposed category: 2B.
- Route type: combined.
- Technical section height difference — 440 m; technical section length — 475 m; section lengths: category 2 — 250 m, category 3 — 225 m; Average slope of the key section — 46°; entire route — 35°.
- Equipment used on the route:
- anchor pitons — 5 pcs.
- friends and chocks — 8 pcs.;
- left behind — 0 pcs.
- Team's climbing time: 3 h 30 min (excluding approach and descent).
- First ascent, winter March 25, 2017: Leader: Orlov V.S. — 2nd sports category; Participant: Kovalev E.V. — 2nd sports category; Participant: Mendin V.Yu. — 2nd sports category. Second ascent, summer. Date: July 23, 2017. Kovalev Evgeny — 2nd sports category, Koksharov Igor — 1st sports category, Yurko Anatoly — 3rd sports category, Grinevich Sergey — 3rd sports category, Egorov Vyacheslav — 3rd sports category, Khairdinov Artur — 3rd sports category.
- Coach: Proklov V.G.
- Time on the route: Start of ascent — 8:00; Reach the summit — 11:30; Return to base camp — 14:00. Descent from the summit: via the NE ridge of the Eastern spur of Aikuayvenchorr, then to the railway tracks and down to the road to the Fosagro mine.
- Organization: Federation of Mountaineering and Rock Climbing of the Arkhangelsk Region.
- Responsible for the report: Orlov V.S., orlovvss@yandex.ru
Information about the Area
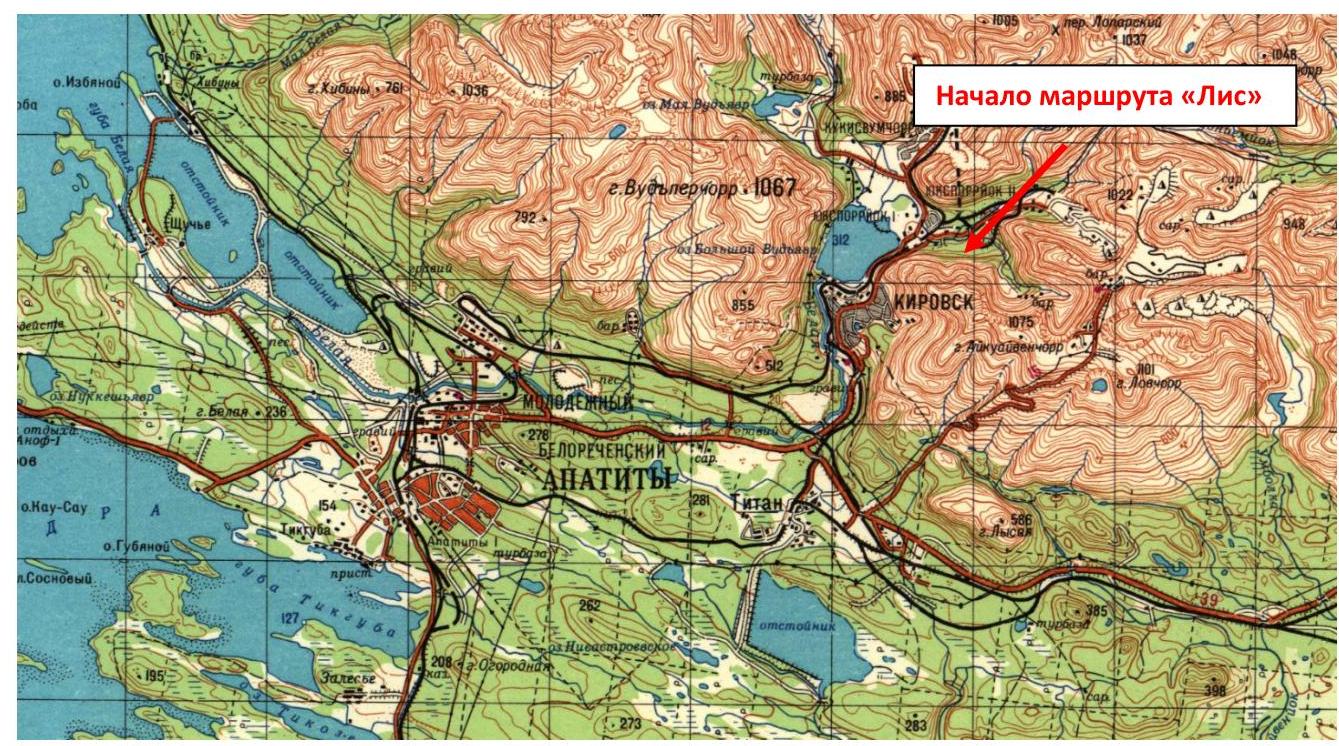 Fig. 1. Map of the area (fragment, scale — 1:50 000)
Fig. 1. Map of the area (fragment, scale — 1:50 000)
 Fig. 2. Route line (Google Maps 3D)
Fig. 2. Route line (Google Maps 3D)
 Fig. 3. View of the route from the railway tracks
Fig. 3. View of the route from the railway tracks
 Fig. 4. View of the route from the starting point
Fig. 4. View of the route from the starting point
Route Description
Approach: to the railway bridge of the mine, along the tracks to the 165th pole, then through the forest along the trail to the intersection with the old winter road (into the VMF Cirque), then move to the foot of the spur (1–1.5 hours); Start of the route from a large solitary stone. From it, move upwards on snow, in summer — on talus 150 m, 25°.
R0–R1: At the beginning of the rocky rib, there is a station on the right side. Move along the rib with belay! Be cautious of moss, and possible ice formation in winter. Belay is scarce. Climbing category 1–2, 60 m, angle 30° — move to a clear platform under a small wall. Station under chocks and pitons. (Control tour #1 — can on a piton).
R1–R2: Move right along the rib, up to the base of the internal corner (in summer, move up under the wall and traverse right). Attention: rare belay and rockfall from the right. Station under the internal corner. 60 m, 25°, category 1–2. The platform for the station is small (Control tour #2 — can on a piton).
R2–R3: The first key — internal corner, height 6 m, category 3, 65°. In summer, without entering the corner, ascend along the corner of the bastion, 6 m, category 3, 80°, belay on pitons, traverse left along the ledge 10 m. Exit to the beginning of the "fox" field. Station on a rock. Convenient bivouac site.
R3–R4: Crossing the field to the beginning of the rocky bastion. (In winter, avalanche danger, belay required). 60 m, category 1, 25°. Control tour #3.
R4–R5: Traverse right under the wall of the bastion. 50 m, 25°, category 2. Station site not reaching the pronounced internal corner with a grotto.
R5–R6: Move to the grotto 10 m, category 2, 30°. Then into the internal corner via a system of ledges. Category 3–4, 20–25 m, 40–55°, then exit to the upper part of the rock blocks. 20 m, 15–20°, category 1. In summer, move to the grotto 10 m, traverse right 25 m, ascend along the destroyed rocks, bypassing the stone finger 30 m. On the left, passage into the crevice, rockfall danger, 20°, 5 m, then a series of ledges and small walls, climbing category 1–2, 20 m. Exit to the upper part. Then exit to the plateau and simultaneous movement to the summit.
Descent: via the NE ridge of the Eastern spur of Mt. Aikuayvenchorr. Then to the railway tracks and down to the road to the mine.
Emergency descent: via the ascent route.
Recommendations
- Recommended climbing time — 4 hours.
- The key section is climbed with climbing techniques.
- The route is logical, safe, with bivouac sites for groups.
- 3 control tours established at key locations.
Route Diagram in UIAA Symbols
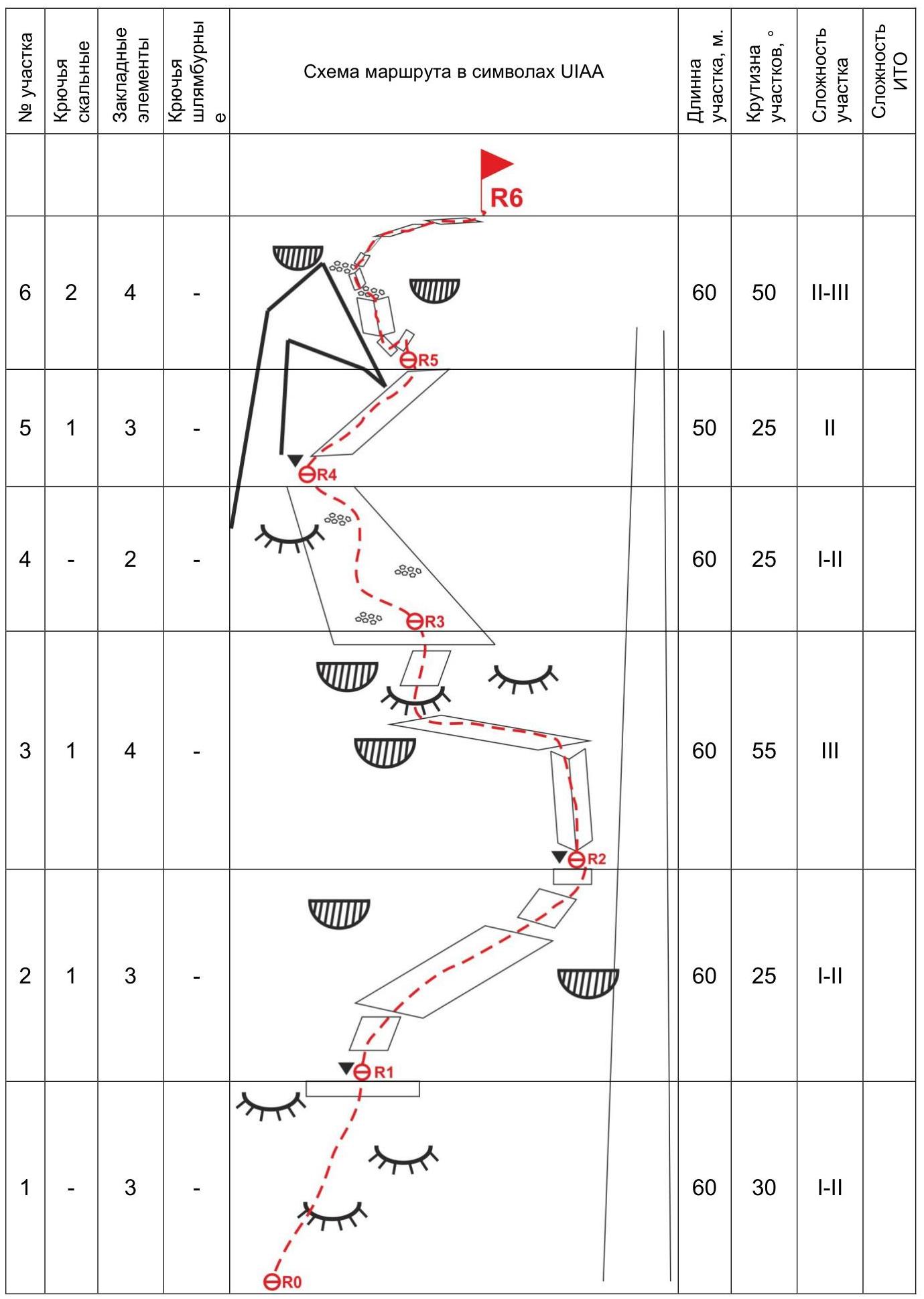
| Section # | Rock Pitons | Chocks | Bolt Pitons | Section Length, m | Slope, ° | Section Difficulty | ITD Difficulty |
|---|---|---|---|---|---|---|---|
| 6 | 2 | 4 | - | 60 | 50 | 2–3 | |
| 5 | 1 | 3 | - | 50 | 25 | 2 | |
| 4 | - | 2 | - | 60 | 25 | 1–2 | |
| 3 | 1 | 4 | - | 60 | 55 | 3 | |
| 2 | 1 | 3 | - | 60 | 25 | 1–2 | |
| 1 | - | 3 | - | 60 | 30 | 1–2 |
Route Photo Illustrations


Digitized by Google

Digitized by Google

Digitized by Google



Digitized by Google






Digitized by Google

1. Introduction
This document provides an overview of key concepts and methodologies used in the study of quantum mechanics. It covers:
- Fundamental principles
- Mathematical formulations
- Practical applications
2. Fundamental Principles
2.1 Wave-Particle Duality
Quantum mechanics introduces the concept of wave–particle duality, where particles such as electrons and photons exhibit both wave-like and particle-like properties. This duality is central to understanding the behavior of quantum systems.
2.2 Superposition
The principle of superposition states that a quantum system can exist in multiple states simultaneously until it is measured. This is mathematically represented by a wave function, denoted as $\vert\psi\rangle$.
2.3 Uncertainty Principle
The Heisenberg Uncertainty Principle states that it is impossible to simultaneously know the exact position and momentum of a particle. This is expressed as: Δx ⋅ Δp ≥ ℏ/2, where
- Δx — uncertainty in position,
- Δp is the uncertainty in momentum,
- ℏ is the reduced Planck constant.
3. Mathematical Formulations
3.1 Schrödinger Equation
The Schrödinger equation is a fundamental equation in quantum mechanics that describes how the quantum state of a physical system changes over time. It is given by: iℏ ∂/∂t Ψ(r, t) = Ĥ Ψ(r, t) where
- Ψ(r, t) is the wave function,
- Ĥ is the Hamiltonian operator.
3.2 Dirac Notation
Dirac notation is a convenient way to represent quantum states and operators. It uses bra–ket notation, where a quantum state is described by a ket, and bra–ket notation is used to represent quantum states and operators.
4. Practical Applications
4.1 Quantum Computing
Quantum computing leverages the principles of superposition and entanglement to perform computations that are infeasible for classical computers. Quantum bits, or qubits, are the fundamental units of quantum information.
4.2 Quantum Cryptography
Quantum cryptography uses the principles of quantum mechanics to secure communication. Quantum key distribution (QKD) is a cornerstone of quantum cryptography.
4.3 Quantum Cryptography
Quantum cryptography uses the principles of quantum mechanics to secure communication. Quantum key distribution (QKD) is a method of secure communication.
5. Conclusion
Quantum mechanics is a cornerstone of modern physics, providing a framework for understanding the behavior of particles at the smallest scales. Its principles and mathematical formulations have led to groundbreaking technologies and continue to inspire new research and development.
6. References
- Griffiths, D. J. (2005). Introduction to Quantum Mechanics. Pearson.
- Shankar, R. (2012). Principles of Quantum Mechanics. Plenum Press.





Digitized by Google































